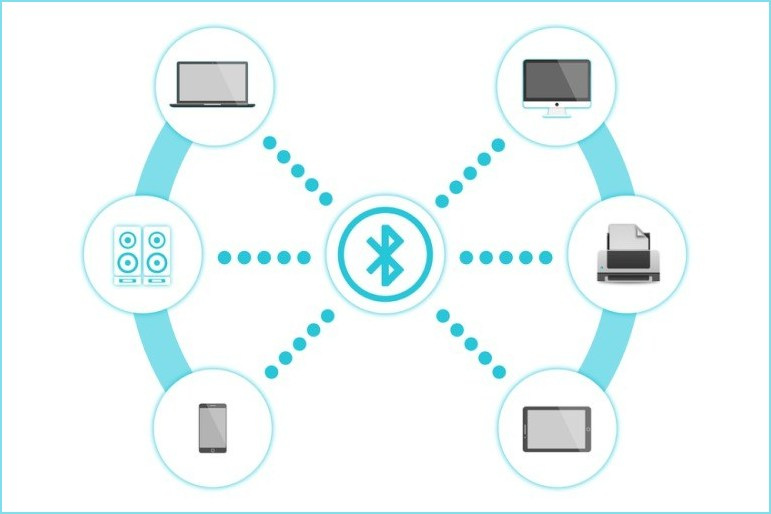
Bluetooth is a high-speed wireless communication technology that uses low-power radio waves in order to allow two electronic de...
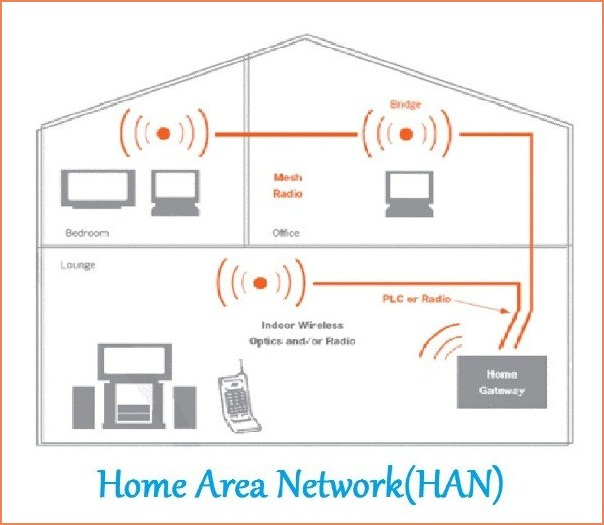
Short for a home area network, a HAN is a small type of network that is designed to cover a home, as suggested in the name. It....
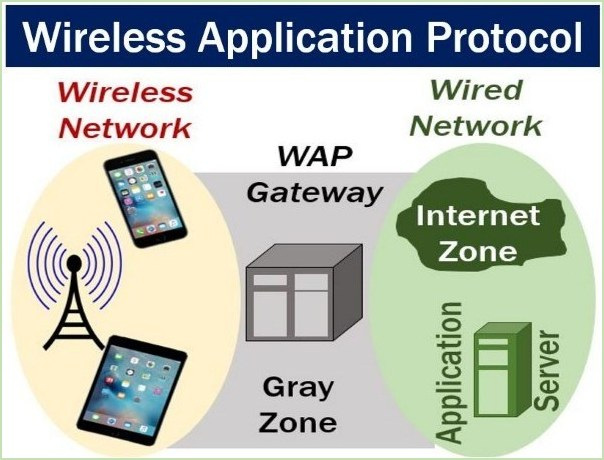
A wireless application protocol, also known as a WAP is a technology that enables the retrieval of information over a mobile wi...

Short for a virtual private network, a VPN provides a secure and private connection over a public, business, or home network by...

An internet service provider, also known as an internet network service provider is a company that provides internet access for both homes and business...
A domain registrant is a user or company that owns and conducted the registration of a certain domain name. Domain registrants....

Freenom (also known as dot.tk) is a free domain provider that offers five TLDs for free, which include .tk, .ml, .cf, .ga, and .gq. Freenom is known as 'th...
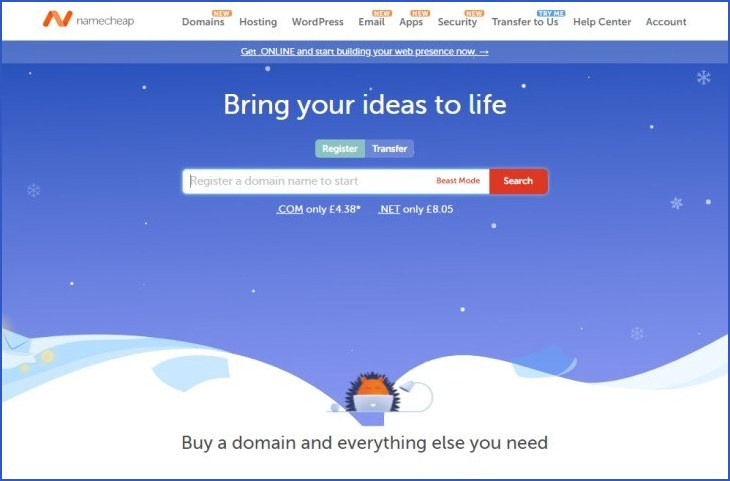
A domain registrar is a company that allows users to register domain names, which are URLs that are made up of alphanumeric let...

A subdomain, also known as a child domain refers to a domain that is part of another domain, such as the address of this websi...

Domain squatting, also known as cybersquatting is the act of registering a domain with the sole purpose of preventing another u...

Typosquatting is the act of registering misspellings or typos of common domain names in the hope that a user mistypes the URL and visits the typosquatted website. Such domains could 'phish' for other people's details and try to trick them into entering...

A domain name is an address that can be seen in the URL field of the web browser. Domain names have a custom name, usually the....
Network Services Network Setups Network Standards Network Hardware Network Identifiers Network Software Internet Protocols Internet Organisations Data Transmission Technologies Web Development Web Design Web Advertising Web Applications Web Organisations Web Technologies Web Services SEO Threats To Systems, Data & Information Security Mechanisms & Technologies Computer Hardware Computer Software Ethics & Sustainability Legislation & User Data Protection