
A firewall is a type of computer network security system that puts a restriction on internet traffic entering, leaving, and wit...

Short for hypertext transfer protocol, HTTP is a protocol that is used for the transmission of information between web browsers...
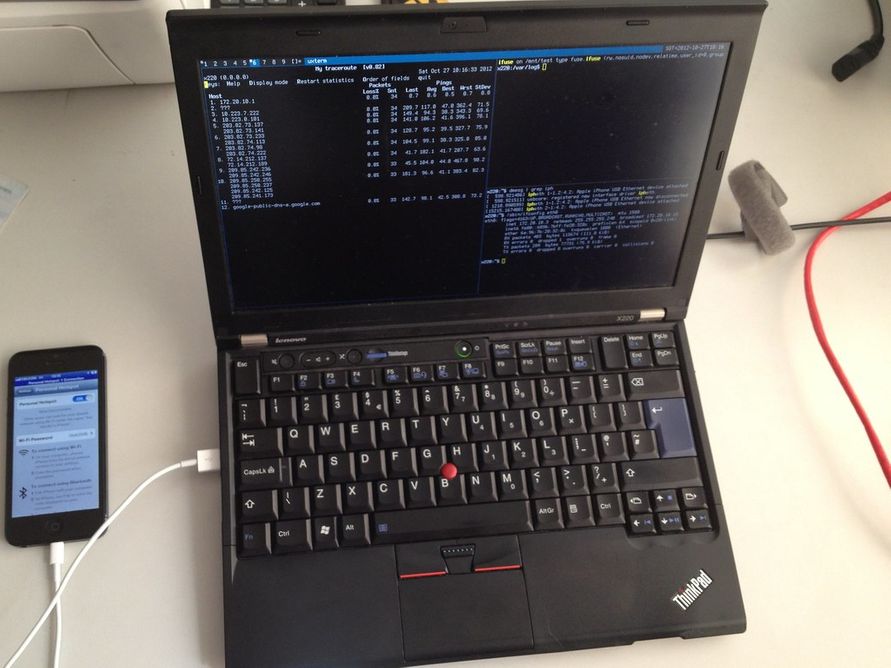
Tethering, also known as phone-as-modem (PAM) is the sharing of the internet connection of a mobile phone to a connected comput...
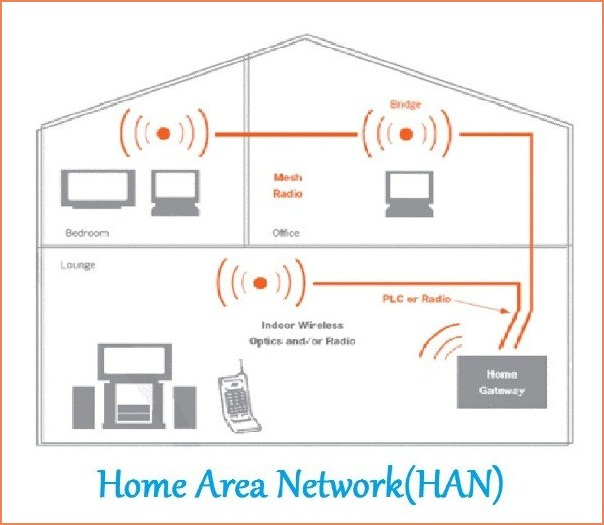
Short for a home area network, a HAN is a small type of network that is designed to cover a home, as suggested in the name. It....

Short for a wide area network, a WAN is a term that describes a large computer network that is fixed to a single location and covers a wide geographical area, such as multiple cities. It is the opposite of a LAN (local...

Short for internet protocol address, an IP address is a string of four unique numbers, separated by full stops that are assigne...
An expired domain refers to a domain name that has been registered by someone, but hasn't been renewed before its expiry date.....
WHOIS is a protocol that first started in 1982, containing a public database of information about all registered domain names.....

A subdomain, also known as a child domain refers to a domain that is part of another domain, such as the address of this websi...

Domain squatting, also known as cybersquatting is the act of registering a domain with the sole purpose of preventing another u...

Typosquatting is the act of registering misspellings or typos of common domain names in the hope that a user mistypes the URL and visits the typosquatted website. Such domains could 'phish' for other people's details and try to trick them into entering...

A domain name is an address that can be seen in the URL field of the web browser. Domain names have a custom name, usually the....
Network Services Network Setups Network Standards Network Hardware Network Identifiers Network Software Internet Protocols Internet Organisations Data Transmission Technologies Web Development Web Design Web Advertising Web Applications Web Organisations Web Technologies Web Services SEO Threats To Systems, Data & Information Security Mechanisms & Technologies Computer Hardware Computer Software Ethics & Sustainability Legislation & User Data Protection